In today’s digital age, cybersecurity is more important than ever. As technology advances, so do the threats and vulnerabilities. This article will explore the latest cybersecurity threats and how to protect against them.
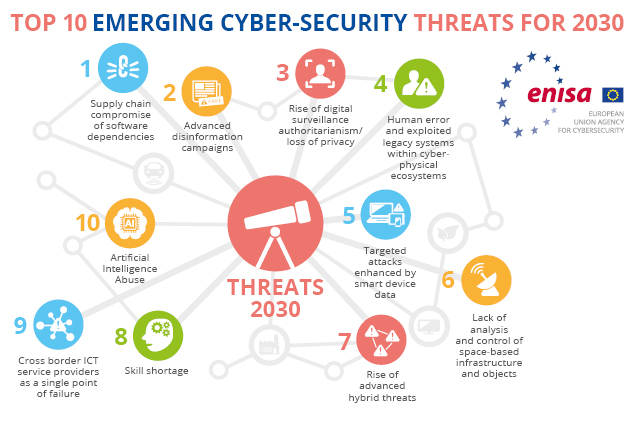
Credit: www.enisa.europa.eu
What Are Cybersecurity Threats?
Cybersecurity threats are malicious activities aimed at stealing data, damaging systems, or disrupting operations. These threats come in many forms and can target individuals, businesses, and governments.
Common Types of Cybersecurity Threats
Cybersecurity threats can be categorized into several types. Here are some of the most common ones:
- Malware: Malicious software designed to harm or exploit devices.
- Phishing: Fraudulent attempts to obtain sensitive information by pretending to be a trustworthy entity.
- Ransomware: Malware that encrypts data and demands payment for its release.
- Denial of Service (DoS): Attacks that overwhelm a system, making it unavailable.
- Man-in-the-Middle (MitM): Attacks where the attacker intercepts communication between two parties.
Emerging Cybersecurity Threats
As technology evolves, new cybersecurity threats emerge. Here are some of the latest threats:
1. Internet Of Things (iot) Vulnerabilities
IoT devices are becoming more common in homes and businesses. These devices often lack proper security measures, making them easy targets for hackers.
2. Ai-powered Attacks
Artificial Intelligence (AI) is being used by cybercriminals to create more sophisticated attacks. AI can automate tasks, making attacks faster and harder to detect.
3. Deepfake Technology
Deepfakes are manipulated videos or images created using AI. These can be used to spread misinformation or impersonate individuals.
4. Cloud Security Threats
More businesses are moving to the cloud. While this offers many benefits, it also introduces new security risks. Unauthorized access and data breaches are major concerns.
5. Supply Chain Attacks
Attackers target less secure elements of a supply chain to gain access to larger networks. These attacks can be difficult to detect and prevent.

Credit: www.unsdglearn.org
Vulnerabilities in Cybersecurity
Vulnerabilities are weaknesses in a system that can be exploited by threats. Here are some common vulnerabilities:
- Outdated Software: Old software may have unpatched security flaws.
- Weak Passwords: Simple passwords are easy to guess or crack.
- Insufficient Encryption: Poor encryption can be easily bypassed.
- Unsecured Networks: Open or poorly secured networks are vulnerable to attacks.
- Human Error: Mistakes made by users can lead to security breaches.
How to Protect Against Cybersecurity Threats
Protecting against cybersecurity threats requires a multi-faceted approach. Here are some steps you can take:
1. Keep Software Updated
Always install the latest updates for your software. Updates often include security patches that fix vulnerabilities.
2. Use Strong Passwords
Create complex passwords that are hard to guess. Use a combination of letters, numbers, and special characters.
3. Enable Two-factor Authentication (2fa)
2FA adds an extra layer of security. It requires not only a password but also a second piece of information, like a code sent to your phone.
4. Use Antivirus Software
Antivirus software can detect and remove malware. Make sure it is always up to date.
5. Secure Your Network
Use strong encryption for your Wi-Fi network. Change the default password of your router.
6. Educate Yourself And Your Team
Awareness is key. Learn about common threats and how to avoid them. Educate your team on best practices.
Frequently Asked Questions
What Are The Latest Cybersecurity Threats?
New threats include ransomware, phishing attacks, and IoT vulnerabilities. Staying updated is crucial for protection.
How Can I Protect Against Ransomware?
Regularly back up data, use strong passwords, and update software. Employ reliable antivirus and anti-malware tools.
Why Is Phishing Still Effective?
Phishing exploits human psychology and trust. Users often click on malicious links unknowingly, compromising security.
What Are Iot Vulnerabilities?
IoT devices often lack strong security measures. They can be hacked, leading to data breaches and unauthorized access.
Conclusion
Cybersecurity threats and vulnerabilities are constantly evolving. Staying informed and taking proactive measures can help protect against these threats. Remember to update your software, use strong passwords, and educate yourself on the latest threats. By doing so, you can keep your data and systems safe.
References
Here are some useful resources to learn more about cybersecurity:
